Explain Different Types of Computer Forensics Technology
Cryptographic algorithms are used for important tasks such as data encryption authentication and digital signatures but one problem has to be solved to enable these algorithms. There is no one single parameter that we can.

02 Types Of Computer Forensics Technology Notes
Definition of copy constructor is given as A copy constructor is a method or member function which initialize an object using another object within the same class.

. For example reading up on different types of cybersecurity certification can give you an idea of the scope of the field and the types of skills that can help you land a job. NEW CLIP ART including diver studentsEach brain break is accompanied by a description of how to do the exercise that can be glued onto. In the six week course using interactive learning tools we will cover the scientific principles underlying forensic pathology medical examination in cases of sexual offences bite.
Topics include properties of solutions acids and bases kinetics equilibrium thermodynamics oxidation reduction ionic and redox equations and electrochemistry. Explore the models implementation and types of access control including administrative physical and. You focus on detecting the misuse of computer systems via the internet and personal users.
This course investigates the use of computers to prevent and solve crime. Also there are also a wide variety of different processor types tiers and companies to factor in as well. Undergraduate This course continues the examination of principles and applications of chemistry that was begun in CHM150.
A class with two or more construct functions with the same name but with different parameters or arguments and other data types is called Constructor overloading. This is a collection of 65 different Brain Breaks for the classroom. Terence Spies in Computer and Information Security Handbook Third Edition 2017.
Binding cryptographic keys to machine or user identities. Cyber Novice February 2 2022. Understanding the Incident Response Life Cycle Incident Handling March 30 2022.
Before you start classes have some fun going down. Read more about Kingston University Londons Cyber Security Digital Forensics BScHons degree. Public key infrastructure PKI systems are.
The Six Types of Cyberattacks Youre Most Likely to Face. Access control involves identifying the security access of a person within an organization. The database schema is its structure described in a formal language supported by the database management system DBMS.
Our BSc Cyber Security and Digital Forensics will develop your theoretical knowledge while you gain the skills practical experience and certifications to excel in areas that range from compliance management to cyber forensics and everywhere in between. Computer forensics also known as computer forensic science is a branch of digital forensic science pertaining to evidence found in computers and digital storage mediaThe goal of computer forensics is to examine digital media in a forensically sound manner with the aim of identifying preserving recovering analyzing and presenting facts and opinions about the. Why study cyber security and digital forensics with us.
In researching certification you might also learn the sort of work you will be doing as a cybersecurity specialist or key terms that you will come across. 000 Skip to 0 minutes and 0 seconds Project 39A National Law University Delhi and Eleos Justice at Monash University present to you this course - Decoding Forensics for Legal Professionals. The term schema refers to the organization of data as a blueprint of how the database is constructed divided into database tables in the case of relational databasesThe formal definition of a database schema is a set of formulas sentences called.
These can be used as transitions breaks in the middle of an activity something to raise or lower the energy of the group team-building activities and moreUPDATE 72020. Top Job Roles for Certified Cybersecurity Technicians Cybersecurity Technician. The Digital Forensics Essentials course provides the necessary knowledge to understand the Digital Forensics and Incident Response disciplines how to be an effective and efficient Digital Forensics practitioner or Incident Responder and how to effectively use digital evidence.

Types Of Threats Found Online Types Of Malware Threats You Need To Protect Against Cyber Security Awareness Computer Security Cyber Security Technology

The Ultimate Guide What Is Computer Forensics Forensic Control

02 Types Of Computer Forensics Technology Notes

02 Types Of Computer Forensics Technology Notes

Pin By Moritz C On Computer Forensics Computer Forensics Forensics Digital Footprint

Various Types Of Computer Forensics Download Scientific Diagram
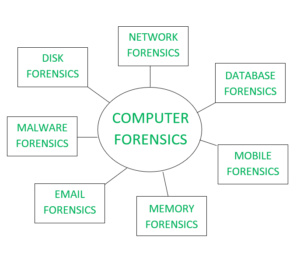
Computer Forensics Techniques Geeksforgeeks
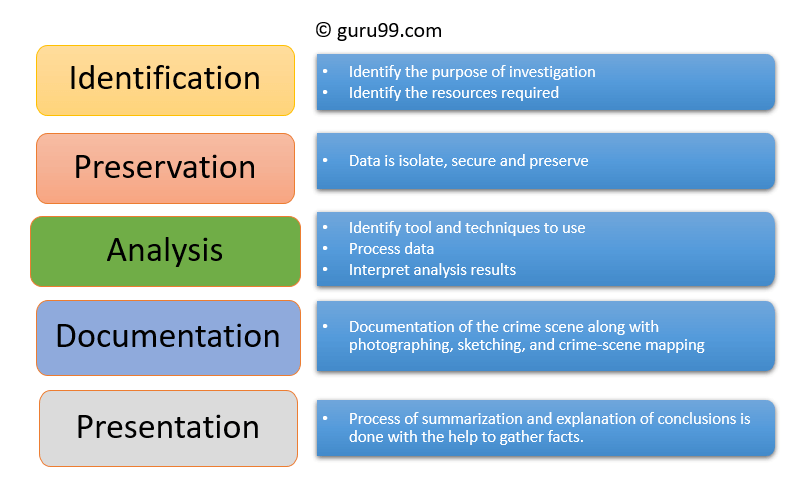
What Is Digital Forensics History Process Types Challenges

02 Types Of Computer Forensics Technology Notes

Pin By Swailes Company Inc On Technology Forensics Criminal Justice Criminal Psychology

Pin On Criminal Justice Computer Forensics Cyber Crime

Issues Facing Computer Forensics E Spin Group

02 Types Of Computer Forensics Technology Notes

Main Branches Of Digital Forensics Download Scientific Diagram

Top 10 Computer Forensics Tools For Analyzing A Breach Computer Forensics Forensics Network Security

What Is Digital Forensics Process Tools And Types Computer Forensicsoverview Recfaces

Digital Forensics Analyst And Miracle Worker Phone Case Forensics In 2022 Phone Cases Cool Phone Cases Phone


Thanks for sharing this update!
ReplyDeleteThat was very interesting
cyber security penetration testing training